Get records from Kinesis cross-count
Architecture
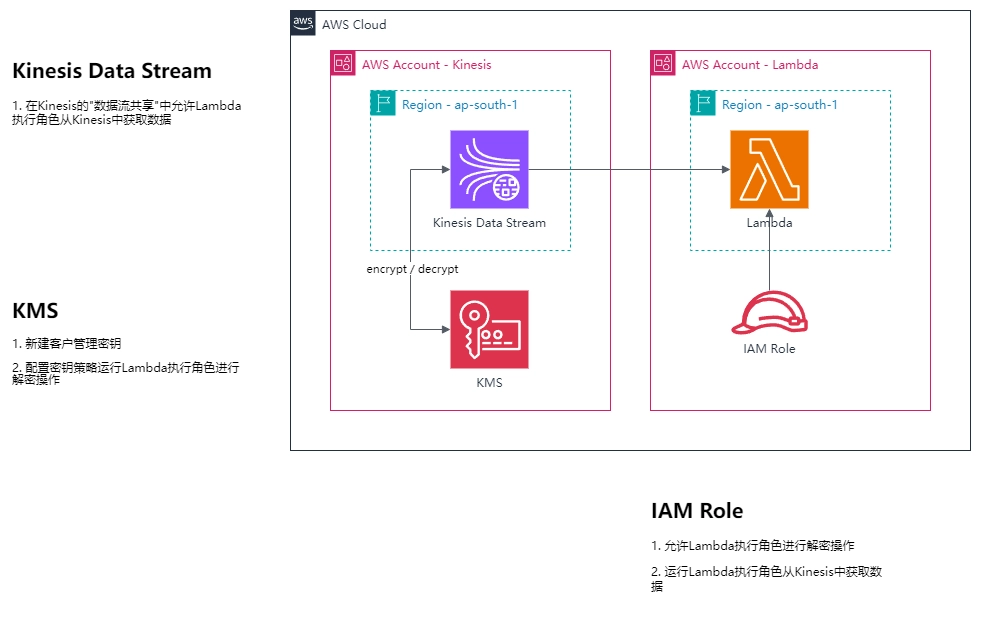
Setup
Kinesis data stream sharing policy
{
"Version": "2012-10-17",
"Statement": [
{
"Sid": "StreamReadStatementID",
"Effect": "Allow",
"Principal": {
"AWS": "arn:aws:iam::167439876321:role/LambdaRoleForCrossAccountKinesisDataStream"
},
"Action": [
"kinesis:GetRecords",
"kinesis:GetShardIterator",
"kinesis:DescribeStream",
"kinesis:DescribeStreamSummary",
"kinesis:ListShards"
],
"Resource": "arn:aws:kinesis:ap-south-1:842676014633:stream/KinesisDataStreamCrossAccount"
}
]
}
KMS key policy
{
"Sid": "Allow Lambda Role",
"Effect": "Allow",
"Principal": {
"AWS": "arn:aws:iam::167439876321:role/LambdaRoleForCrossAccountKinesisDataStream"
},
"Action": "kms:Decrypt",
"Resource": "*"
}
Lambda role permissions
-
Attach the
AWSLambdaKinesisExecutionRoleAWS managed policy to the Lambda execution role -
Attach the
kms:Decryptpermission to the Lambda execution role
{
"Version": "2012-10-17",
"Statement": [
{
"Sid": "VisualEditor0",
"Effect": "Allow",
"Action": "kms:Decrypt",
"Resource": "arn:aws:kms:ap-south-1:842676014633:key/83220705-71c1-4000-9d0f-d041c25675d6"
}
]
}
Test
aws kinesis put-record \
--stream-name KinesisDataStreamCrossAccount \
--data aGVsbG8= \
--partition-key 0